DOD Adjudicative Elements
The topics or "issues" listed below are the primary factors by which Department of Defense (DoD) personnel security specialists (adjudicators) will either grant or deny your application for a security clearance. OPM investigators (National Background Investigations Bureau plus contractors CACI, KeyPoint Government Services, CSRA and Securitas) also utilize these 13 Adjudicative Guidelines to "flag" or alert adjudicators to issues in your case file.
 Personal Subject Interview
Personal Subject Interview
What most people do not know is that within each topic or issue, there are between 6 and 10 sub-topics or issues. These sub-topics and issues are then categorized within a range of values. This range of values will indicate the level of severity per issue or topic. Your topic or issue will range anywhere from not severe (You have nothing to worry about), to very severe (Your security clearance application has a high probability of being denied.)
A personnel security clearance is an administrative determination by a certified adjudicator that an individual is eligible under national security standards for access to classified information. In order to make this determination, a personnel security background investigation is conducted. The information collected must be sufficient to allow an affirmative or negative determination of a person's eligibility for access to classified information. The security clearance process begins when a company, government agency or military branch determines that an employee or candidate for employment requires a personnel security clearance to access classified information in order to perform the duties of his or her position.
The adjudication process seeks reasonable assurance that persons granted access to classified information are persons:
“...whose personal and professional history affirmatively indicates loyalty to the United States, strength of character, trustworthiness, honesty, reliability, discretion and sound judgment, as well as freedom from conflicting allegiances and potential for coercion and willingness and ability to abide by regulations governing the use, handling and protection of classified information.” Source: Executive Order 12968, Access to Classified Information, dated August 4, 1995.
The 13 Adjudicative Guidelines
The following adjudicative guidelines are established for all U.S. government civilian and military personnel, consultants, contractors, employees of contractors, licensees, certificate holders or grantees and their employees and other individuals who require access to classified information. They apply to persons being considered for initial or continued eligibility for access to classified information, to include sensitive compartmented information (SCI) and special access programs (SAPs), and are to be used by government departments and agencies in all final clearance determinations. Government departments and agencies may also choose to apply these guidelines to analogous situations regarding persons being considered for access to other types of protected information.
Decisions regarding eligibility for access to classified information take into account factors that could cause a conflict of interest and place a person in the position of having to choose between his or her commitments to the United States, including the commitment to protect classified information, and any other compelling loyalty. Access decisions also take into account a person's reliability, trustworthiness and ability to protect classified information. No coercive policing could replace the self-discipline and integrity of the person entrusted with the nation's secrets as the most effective means of protecting them. When a person's life history shows evidence of unreliability or untrustworthiness, questions arise whether the person can be relied on and trusted to exercise the responsibility necessary for working in a secure environment where protecting classified national security information (CNSI) is paramount.
Guideline A: Allegiance to the United States
An applicant must be of unquestioned allegiance to the United States. Any reason to suspect otherwise creates doubt about the applicant's willingness to safeguard classified national security information (CNSI).  Allegiance is the loyalty that a citizen owes to his or her country. If allegiance to the United States is in doubt, an individual's willingness to safeguard classified information is also in doubt.
Allegiance is the loyalty that a citizen owes to his or her country. If allegiance to the United States is in doubt, an individual's willingness to safeguard classified information is also in doubt.
There is considerable overlap between the Allegiance Guideline and the Foreign Influence and Foreign Preference Guidelines. It is principally an Allegiance issue when an American citizen uses force or violence in seeking to overthrow or influence the U.S. Government, prevent others from exercising their constitutional rights or to harm deliberately the United States. It is principally a Foreign Influence or Foreign Preference issue when an individual shows a preference for a foreign country, serves a foreign interest or is vulnerable to foreign influence that puts protected information at risk. Some cases are adjudicated under all three guidelines.
Guideline B: Foreign Influence
Foreign contacts and interests become a security concern if an applicant has divided loyalties or if foreign financial interests can be manipulated or induced to help a foreign person, group, organization or government in a way that is not in the interests of the United States. The adjudicative guideline specifies that foreign contacts and interests may be a security concern under the following circumstances: The individual "has divided loyalties or foreign financial interests"; The individual "may be manipulated or induced to help a foreign person, group, organization or government in a way that is not in U.S. interests"; The individual "is vulnerable to pressure or coercion by any foreign interest".
 The adjudicative guideline also states that “Adjudication under this Guideline can and should consider the identity of the foreign country in which the foreign contact or financial interest is located, including, but not limited to, such considerations as whether the foreign country is known to target American citizens to obtain protected information or is associated with a risk of terrorism.”
The adjudicative guideline also states that “Adjudication under this Guideline can and should consider the identity of the foreign country in which the foreign contact or financial interest is located, including, but not limited to, such considerations as whether the foreign country is known to target American citizens to obtain protected information or is associated with a risk of terrorism.”
Guideline C: Foreign Preference
If an applicant's behavior indicates a preference for a foreign country over the United States, then the applicant may be prone to providing information or making decisions that are harmful to U.S. interests. The applicant's preference for a foreign country must be established by adequate evidence of heightened risks to national security. It is not prohibited for a U.S. applicant to hold dual citizenship since this does not establish a preference for a foreign country.

Foreign Preference is an issue whenever a person acts in a way that indicates a possible preference for a foreign country over the United States. Such actions raise questions about a person's loyalty & allegiance and how the person would behave if faced with a conflict between the interests of the United States and the interests of a foreign person, organization or country. A preference for a foreign entity may cause a person to make decisions that are contrary to the interests of the United States.
Guidelines A, B and C are known as ALLEGIANCE ISSUES.
Guideline D: Sexual Behavior
Sexual behavior that involves a criminal offense; indicates a personality or emotional disorder; reflects a lack of judgment or discretion; or may subject an applicant to undue influence or coercion, exploitation or duress can raise questions about the applicant's reliability, trustworthiness and ability to protect classified national security information (CNSI). No adverse inference concerning the standards in this guideline may be made solely on the basis of the sexual orientation of the individual.

Most scientific research and past espionage cases show that the connection between sexual behavior and personnel security is far more complex than the simple notion that "normal" sex is acceptable and "nonconforming" sexual practices are a security risk. Self-control, social maturity, strength of character and overall psychological adjustment are more important security indicators than the specific sexual practices in which people engage. Sexual orientation or preference may not be used as a basis for disqualification in adjudicating eligibility for security clearance.
Guideline E: Personal Conduct
Conduct involving questionable judgment, lack of candor, dishonesty or unwillingness to comply with regulations can raise questions about an applicant's reliability, trustworthiness and ability to protect classified national security information (CNSI). Any failure to provide truthful and candid answers during the security clearance process is of particular interest.
 The following actions may result in unfavorable clearance action or administrative termination of further processing: Refusal or failure without reasonable cause to undergo/cooperate with security processing (e.g., meeting for a Subject Interview, signing forms or releases, cooperating with a medical or psychological evaluation); Refusal to provide truthful answers in connection with a personnel security or trustworthiness determination.
The following actions may result in unfavorable clearance action or administrative termination of further processing: Refusal or failure without reasonable cause to undergo/cooperate with security processing (e.g., meeting for a Subject Interview, signing forms or releases, cooperating with a medical or psychological evaluation); Refusal to provide truthful answers in connection with a personnel security or trustworthiness determination.
The Personal Conduct adjudicative guideline covers unreliable or untrustworthy behavior not considered under other guidelines, or which falls below the threshold for action under any other single guideline. It provides a means for adjudicators to consider a pattern of unreliable and untrustworthy behavior that may encompass multiple guidelines. Importantly, the Personal Conduct guideline also covers vulnerability to coercion, exploitation or duress. Protection of classified information requires compliance with a complex set of rules and regulations. Willingness and ability to comply with rules and regulations is, therefore, an important qualification for access to classified information.
Any conduct that indicates disrespect for rules and regulations can be a security concern under Personal Conduct as well as several other guidelines. Honesty and integrity are other important qualifications. Many people during the course of their lives are beset by problems or stressors that tempt them to engage in improper or illegal behavior. The ability to weather these situations without engaging in improper or illegal activity depends, in large part, upon a person's basic character and integrity. These and other types of conduct may raise questions about a subject's judgment, trustworthiness or reliability, but may not be disqualifying by themselves. They may, however, contribute to an adverse adjudicative decision if they are part of a pattern of undesirable behavior that casts doubt on the subject's willingness or ability to safeguard classified information.
Guideline F: Financial Considerations
 Failure or inability to live within one's means, satisfy debts or meet financial obligations may indicate poor self-control, lack of judgment or unwillingness to abide by rules and regulations, all of which can raise questions about an applicant's reliability, trustworthiness and ability to protect classified national security information (CNSI). An individual who is financially overextended is at risk of having to engage in illegal acts to generate funds. Compulsive gambling is a concern as it may lead to financial crimes including espionage. Affluence that cannot be explained by known sources of income is also a security concern. It may indicate proceeds from financially profitable criminal acts.
Failure or inability to live within one's means, satisfy debts or meet financial obligations may indicate poor self-control, lack of judgment or unwillingness to abide by rules and regulations, all of which can raise questions about an applicant's reliability, trustworthiness and ability to protect classified national security information (CNSI). An individual who is financially overextended is at risk of having to engage in illegal acts to generate funds. Compulsive gambling is a concern as it may lead to financial crimes including espionage. Affluence that cannot be explained by known sources of income is also a security concern. It may indicate proceeds from financially profitable criminal acts.
Guidelines D, E and F are known as CHARACTER ISSUES.
Guideline G: Alcohol Consumption
 Some alcohol use is normal, but excessive use can be a serious security concern. Alcohol affects the central nervous system and how the brain functions. Excessive use affects perception, thinking and coordination. It impairs judgment, reduces inhibitions, and increases any tendency toward aggression. Those who abuse alcohol are more likely than others to engage in high-risk, thoughtless or violent behaviors. This increases the risk of unauthorized disclosure of classified information due to impulsive or careless behavior. Excessive alcohol consumption often leads to questionable judgment or the failure to control impulses and can raise questions about an applicant's reliability and trustworthiness. Evidence from past espionage cases indicates that alcohol problems are more prevalent among convicted spies than in the population as a whole.
Some alcohol use is normal, but excessive use can be a serious security concern. Alcohol affects the central nervous system and how the brain functions. Excessive use affects perception, thinking and coordination. It impairs judgment, reduces inhibitions, and increases any tendency toward aggression. Those who abuse alcohol are more likely than others to engage in high-risk, thoughtless or violent behaviors. This increases the risk of unauthorized disclosure of classified information due to impulsive or careless behavior. Excessive alcohol consumption often leads to questionable judgment or the failure to control impulses and can raise questions about an applicant's reliability and trustworthiness. Evidence from past espionage cases indicates that alcohol problems are more prevalent among convicted spies than in the population as a whole.
Guideline H: Drug Involvement
 Executive Order 12564, dated September 15, 1986, establishes the U.S. Government as a drug-free workplace. It declares that "persons who use illegal drugs are not suitable for federal employment." Applicants cannot be held to a no-prior-use standard, but any illegal drug use at all by a current U.S. Government employee or member of the military is a violation of this presidential order. The use of illegal drugs or the misuse of prescription drugs can raise questions about an applicant's reliability and trustworthiness since these actions impair judgment and suggest an inability or unwillingness to comply with laws, rules and regulations. Cleared employees must respect regulations whether they agree with them or not. If they do not respect the rules on use of illegal substances, they may not respect the rules for protection of classified information.
Executive Order 12564, dated September 15, 1986, establishes the U.S. Government as a drug-free workplace. It declares that "persons who use illegal drugs are not suitable for federal employment." Applicants cannot be held to a no-prior-use standard, but any illegal drug use at all by a current U.S. Government employee or member of the military is a violation of this presidential order. The use of illegal drugs or the misuse of prescription drugs can raise questions about an applicant's reliability and trustworthiness since these actions impair judgment and suggest an inability or unwillingness to comply with laws, rules and regulations. Cleared employees must respect regulations whether they agree with them or not. If they do not respect the rules on use of illegal substances, they may not respect the rules for protection of classified information.
Guideline I: Psychological Conditions
Mental health is a security concern because it influences how a person perceives the world, makes decisions and manages stress. The fact that an individual has had, or continues to have, an emotional, mental or psychological condition does not, by itself, preclude granting access to classified information. The issue is whether the individual's condition causes, or may cause, poor judgment or unreliable, untrustworthy or dysfunctional behavior. Certain emotional, mental and personality conditions can impair judgment, reliability or trustworthiness.

A formal diagnosis of a disorder is not required for there to be a concern under this guideline. A qualified mental health professional (e.g., clinical psychologist or psychiatrist) employed or approved by the U.S. Government should be consulted when evaluating potentially disqualifying and mitigating information. Negative inference regarding the standards of this guideline may not be raised solely on the basis of an applicant having sought mental health counseling.
Many people, perhaps most people, experience some form of stress that threatens their self-image at some time in their lives: They experience failure to compete effectively with their peers; perceive injustice at the hands of a supervisor or employing organization; are terminated from a job under circumstances that prompt resentment; feel rejected or betrayed by a spouse; confront serious financial or medical problems; or are tempted by a seemingly easy opportunity for illegal monetary gain.
Emotionally stable and well-adjusted individuals generally respond to these experiences in positive ways; by learning from them, adjusting their expectations, working harder or sticking with their core values. Individuals who are unstable or poorly adjusted, have a significant character weakness or suffer from mental illness may react in ways that are self-destructive, counterproductive or illegal. They may harm the organization by actions that run the gamut from absenteeism to self-serving decisions, theft, fraud, sabotage or espionage.
Guidelines G, H and I are known as HEALTH ISSUES
Guideline J: Criminal Conduct
Criminal activity creates doubt about a person's judgment, reliability and trustworthiness. By its very nature, past or current criminal activity calls into question a person's ability or willingness to comply with laws, rules and regulations. Adjudication standards that disqualify individuals with a significant criminal history are supported by evidence that past adult criminal behavior predicts an increased likelihood of future criminal behavior. It is different with juveniles, however. The vast majority of juvenile offenders get into trouble only once or twice and they stop offending as they mature.
 Screening out applicants with a significant criminal history protects the organization against more than just espionage. Organizations are vulnerable to a wide variety of crimes including embezzlement, procurement fraud, sabotage of computer systems and theft of government property. Other crimes such as drug dealing, illegal gambling, assault on coworkers, theft from other employees and prostitution also affect the workplace. National security organizations have a vested interest in maintaining high standards.
Screening out applicants with a significant criminal history protects the organization against more than just espionage. Organizations are vulnerable to a wide variety of crimes including embezzlement, procurement fraud, sabotage of computer systems and theft of government property. Other crimes such as drug dealing, illegal gambling, assault on coworkers, theft from other employees and prostitution also affect the workplace. National security organizations have a vested interest in maintaining high standards.
Most government organizations and private businesses do not know and cannot measure accurately how much they suffer from theft in the workplace by employees or outsiders. Professional business literature contains many accounts indicating that when companies do gather the necessary data, they are often surprised at the magnitude of losses they have been sustaining.
Guideline K: Handling Protected Information
Deliberate or negligent failure to comply with rules and regulations for protecting classified or other sensitive information raises doubt about an individual's trustworthiness, judgment, reliability or willingness and ability to safeguard such information and is a serious security concern. This includes protecting controlled but unclassified information such as For Official Use Only (FOUO), proprietary, export-controlled or privacy information.
Although the adjudicative process considers trustworthiness and reliability in regards to protecting national security-related information, an applicant's prior history with handling other forms of protected information is relevant (e.g., mishandling proprietary information while employed with a private company).
 Two general types of behaviors related to mishandling protected information are relevant to security: 1) deliberate violation of security rules and regulations and 2) pattern of negligence, carelessness or inattention to following the security rules and regulations. Any deliberate violation of security rules or regulations, including Handling Protected Information during previous employment in the private sector, is a significant concern, as it may indicate indifference toward national security or a general inability or unwillingness to abide by the security regulations.
Two general types of behaviors related to mishandling protected information are relevant to security: 1) deliberate violation of security rules and regulations and 2) pattern of negligence, carelessness or inattention to following the security rules and regulations. Any deliberate violation of security rules or regulations, including Handling Protected Information during previous employment in the private sector, is a significant concern, as it may indicate indifference toward national security or a general inability or unwillingness to abide by the security regulations.
Guideline L: Outside Activities
 Involvement in certain types of outside employment or activities is of security concern if it poses a conflict of interest with an individual's security responsibilities and could create an increased risk of unauthorized disclosure of classified information. It is when an individual's activities present a potential conflict with their role as a clearance holder that a national security concern exists. Conflicts of interest can take many forms, including employment, consulting, volunteering and political activities.
Involvement in certain types of outside employment or activities is of security concern if it poses a conflict of interest with an individual's security responsibilities and could create an increased risk of unauthorized disclosure of classified information. It is when an individual's activities present a potential conflict with their role as a clearance holder that a national security concern exists. Conflicts of interest can take many forms, including employment, consulting, volunteering and political activities.
Of particular concern are three types of role conflict: 1) employment or service with a foreign government, organization or interest group, 2) foreign or domestic outside activities related to the individual's area of expertise and 3) ideological conflict with core concepts of national security.
Guideline M: Use of Information Technology (IT) Systems
 Noncompliance with rules, procedures, guidelines or regulations pertaining to information technology systems may raise security concerns about an individual's reliability and trustworthiness, calling into question the willingness or ability to properly protect sensitive systems, networks and information. Information Technology (IT) Systems include all related computer hardware, software, firmware and data used for the communication, transmission, processing, manipulation, storage or protection of information. Such behavior is sometimes part of a more general pattern of inability or unwillingness to follow rules that should also be evaluated under the Personal Conduct Guideline.
Noncompliance with rules, procedures, guidelines or regulations pertaining to information technology systems may raise security concerns about an individual's reliability and trustworthiness, calling into question the willingness or ability to properly protect sensitive systems, networks and information. Information Technology (IT) Systems include all related computer hardware, software, firmware and data used for the communication, transmission, processing, manipulation, storage or protection of information. Such behavior is sometimes part of a more general pattern of inability or unwillingness to follow rules that should also be evaluated under the Personal Conduct Guideline.
The term information technology systems as used here includes all computer hardware, software, firmware, networks and data used for the communication, transmission, processing, manipulation, storage or protection of information. While not always illegal, misuse of information technology systems is often unethical and usually reflects poor judgment or lack of care in following security rules and regulations.
As we store more and more information in computer databases and as these databases become more closely linked in networks, more people have broader access to more classified and other sensitive information than ever before. This magnifies the amount of damage that can be caused by a single cleared insider working for the other side.
As it becomes easier for people to access computer databases, ease of use means ease of abuse. Using the computer, individual employees can quickly and quietly commit serious crimes that are very difficult to detect. They can steal information, change information or destroy information in automated file systems while sitting at their desk and doing nothing that appears out of the ordinary to casual observers.
Personnel with technical skills and administrative access to a network are also capable of damaging or impairing the operability of critical information systems. There have been numerous cases of such malicious behavior by disgruntled IT professionals with some level of administrative access to a government or corporate system.

Owing to the magnitude of problems that can be caused by misuse of computer systems, all agencies have a vested interest in maintaining a work environment that fosters high standards of computer security. The work environment that tacitly ignores or tolerates petty violations is also the climate where serious violations are most likely to occur.
Guidelines J, K, L and M are known as BEHAVIOR ISSUES
Financial considerations, personal conduct and foreign influence account for approximately 75% of all security clearance denials.
The Adjudicative Process
The adjudicative process is an examination of a sufficient period of a person's life to make an affirmative determination that the person is an acceptable security risk. Eligibility for access to classified information is predicated upon the individual meeting these personnel security guidelines. The adjudication process is the careful weighing of a number of variables known as the whole-person concept. Available, reliable information about the person, past and present, favorable and unfavorable, should be considered in reaching a determination. In evaluating the relevance of an individual's conduct, the adjudicator will consider the 13 Adjudicative Guidelines and cross reference them with the following below-listed 9 Adjudicative Factors:
- The nature, extent, and seriousness of the conduct.
- The circumstances surrounding the conduct, to include knowledgeable participation.
- The frequency and recency of the conduct.
- The individual's age and maturity at the time of the conduct.
- The voluntariness of participation.
- The presence or absence of rehabilitation and other pertinent behavioral changes.
- The motivation for the conduct.
- The potential for pressure, coercion, exploitation, or duress.
- The likelihood of continuation or recurrence.
Each case must be judged on its own merits and final determination remains the responsibility of the specific department or agency. Any doubt concerning personnel being considered for access to classified information will be resolved in favor of the national security.
The ability to develop specific thresholds for action under these guidelines is limited by the nature and complexity of human behavior. The ultimate determination of whether the granting or continuing of eligibility for a security clearance is clearly consistent with the interests of national security must be an overall common sense judgment based upon careful consideration of the 13 adjudicative guidelines, each of which is to be evaluated in the context of the whole person.
Although adverse information concerning a single criterion may not be sufficient for an unfavorable determination, the individual may be disqualified if available information reflects a recent or recurring pattern of questionable judgment, irresponsibility or emotionally unstable behavior. Notwithstanding the whole-person concept, pursuit of further investigation may be terminated by an appropriate adjudicative agency in the face of reliable, significant, disqualifying, adverse information.
Many employees become disloyal after gaining a security clearance. Thus, the applicant clearance process must focus on risk factors that indicate a potential for future betrayal as well as current loyalty. When information of security concern becomes known about an individual who is currently eligible for access to classified information, the adjudicator should consider whether the person:
- voluntarily reported the information;
- was truthful and complete in responding to questions;
- sought assistance and followed professional guidance, where appropriate;
- resolved or appears likely to favorably resolve the security concern:
- has demonstrated positive changes in behavior and employment;
- should have his or her access temporarily suspended pending final adjudication of the information.
If after evaluating information of security concern, the adjudicator decides that the information is not serious enough to warrant a recommendation of disapproval or revocation of the security clearance, it may be appropriate to recommend approval with a warning that future incidents of a similar nature may result in revocation of access.
The complexity of human behavior severely limits any ability to codify such thresholds for making adjudicative decisions. The adjudicator in each case must make what is called a whole-person judgment based on all available information about an individual's reliability and trustworthiness. This includes favorable information, unfavorable information, circumstances that may mitigate the unfavorable information, and circumstances that may affect the credibility of the information.
A fundamental security principle is that all doubts concerning personnel having access to classified data shall be resolved in favor of national security. An equally fundamental legal principle is that access to classified information is a privilege, not a right. No one has a right to a security clearance, but the government is required to follow its own rules so that any decision to deny is made through a reasonable and unbiased process.
The adjudicator is not just a reviewer and reporter of information. The adjudicator is an analyst who forms his or her conclusions and recommendations based on a review of all available information. The role of the adjudicator is to ensure that all doubts concerning personnel being granted eligibility for access to classified information shall be resolved in favor of national security. Access to classified information is a privilege, not a right.
Making judgments that affect the lives and livelihoods of other people imposes a heavy responsibility on adjudicators to protect the rights of individuals as well as the national interest. This responsibility can be unsettling when the proper decision is uncertain. The adjudicator must make a conscientious effort to be sufficiently knowledgeable about the individual, to evaluate the facts fairly and objectively, to seek counsel from knowledgeable supervisors and specialists as appropriate, and to make a balanced and succinct presentation of all relevant factors in each case. An adjudicator must be free of any personal biases, opinions and prejudices when applying the 13 Adjudicative Guidelines.
The typical formula for not just the DoD CAF but for most of the other 22 federal non-IC (Intelligence Community) CAFs would resemble the following:
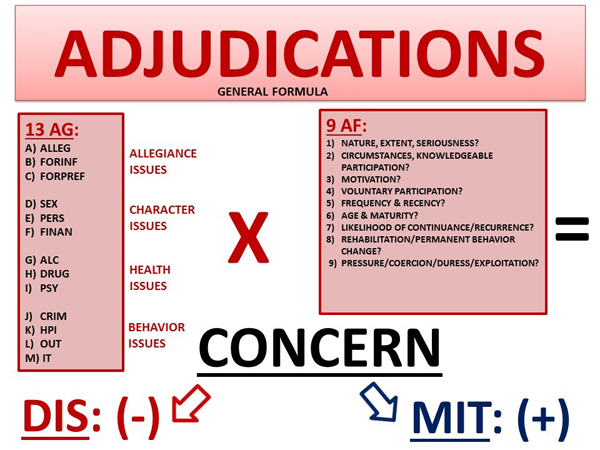
The 13 Adjudicative Guidelines (AG) are cross-referenced with the 9 Adjudicative Factors (AF) to arrive at a CONCERN. Once a CONCERN is identified by a Personnel Security Specialist (Adjudicator) within one of the CAFs, DISQUALIFIERS are then applied to the CONCERN. If MITIGATORS cannot be applied to the noted DISQUALIFIERS, an applicant most likely will be denied a security clearance.
Just like in the field of accounting, where "debits must equal credits", in the field of security clearance adjudications, “DISQUALIFIERS must equal MITIGATORS”, in order to receive a Favorable security clearance decision.
The Whole-Person Concept
Candidates for security clearance are evaluated under a system which provides a balanced assessment of affirmative or positive qualities as well as potentially disqualifying behaviors. These two approaches come together in the "whole person" concept, which is fundamental to the adjudicative process. All information, both favorable and unfavorable, is weighed. A person's strengths are evaluated to assess whether the strengths outweigh the weaknesses.
Three positive qualities, among others, are associated with trustworthiness, reliability and being an overall good security risk. These are: (1) a strong sense of social responsibility; (2) self-control, or the ability to exercise responsible and rational control over one's impulses; and (3) the ability to maintain personal or job commitments over time. These positive qualities may outweigh some unfavorable information. A person with these qualities may not be a security risk even if, for example, he or she were to develop an alcohol problem or serious financial debt.
Social Responsibility
Maintaining security requires following the rules for protection of classified information. The socially responsible person has appropriate respect for authority, comfortably accepts ordinary rules and regulations, and deals fairly with others. This is the opposite of the antisocial person who resists rules and regulations, finds it difficult to conform to society's expectations, and exploits and manipulates other persons.
Self-Control
Security requires the exercise of sound judgment in protecting classified information. Employees whose behavior is under conscious control think before acting, take their duties seriously, and are able to delay immediate gratification of their desires in order to achieve some longer-term goal. They have the self-discipline generally required for success in an academic or career environment. They seldom make impulsive decisions that they regret later.
Capacity for Making Commitment
Obligations that accompany a security clearance involve a lifetime commitment to maintain secrecy. Evidence of ability to maintain commitments to people or organizations is a strong plus in the whole-person judgment. It indicates that the employee-employer relationship, too, is likely to withstand the inevitable rocky periods that crop up in most relationships and which might otherwise cause the employee to turn against the employer. It gets to the very heart of the security issue: Is the subject capable, over a long period of time, of maintaining a commitment to protect classified information under all circumstances?
Sources and Information
A source's impressions, opinions or interpretations are useful to investigators as clues to things that require further investigation, but they are generally not used as a basis for adjudicative action unless they are substantiated by examples of specific behaviors. For example, a source's opinion that the subject is irresponsible should be substantiated by description of specific examples of the subject's irresponsibility, such as moving out of a rental apartment without notice. A source's impression that subject is vindictive could be substantiated by description of threats or destruction of property.
Unfavorable information is more useful when time and frequency are expressed in specific rather than general terms: last week or last year, rather than recently; twice a week or twice a year, rather than frequently.
Most people try to conceal their involvement in illegal, immoral or otherwise embarrassing activities. It follows that such information will be known to few people, and that these are likely to be close associates such as family members, lovers, best friends, teammates or close work colleagues.
The quality and completeness of investigation can be judged, in part, by the extent to which people who have been very close to subject are available as sources. One knowledgeable source who reports credible adverse information may outweigh many acquaintances who claim never to have seen evidence of such behavior. If adverse information comes from a single source, it is necessary to evaluate both the credibility of the source's access to that information and any possible ulterior motives for providing that information.
Adjudications
 Certain positions within DoD entail duties of such a sensitive nature, including access to classified information, that the misconduct, malfeasance or nonfeasance of an incumbent in any such position could result in an unacceptably adverse impact upon the national security of the United States. The DoD CAF at Fort Meade, MD will adjudicate or evaluate an individual's personnel security investigation (PSI) from the Office of Personnel Management (OPM), National Background Investigations Bureau (NBIB). The CAF will render a determination of each individual's eligibility to occupy national security sensitive positions and/or access to classified information, U.S. government buildings and automated information systems (AIS).
Certain positions within DoD entail duties of such a sensitive nature, including access to classified information, that the misconduct, malfeasance or nonfeasance of an incumbent in any such position could result in an unacceptably adverse impact upon the national security of the United States. The DoD CAF at Fort Meade, MD will adjudicate or evaluate an individual's personnel security investigation (PSI) from the Office of Personnel Management (OPM), National Background Investigations Bureau (NBIB). The CAF will render a determination of each individual's eligibility to occupy national security sensitive positions and/or access to classified information, U.S. government buildings and automated information systems (AIS).
Trained adjudicators apply regulations, executive orders and government directives in order to determine the loyalty, trustworthiness and reliability of security clearance applicants.
- Executive Order 12968, "Access to Classified Information," prescribes the process for military and civilian personnel. The process involves the adjudication of the security eligibility of military personnel and civilian employees of the Department of Defense under Executive Order 12968 and DoD Regulation 5200.2-R.
- Executive Order 10865, "Safeguarding Classified Information within Industry," outlines the process for contractors. An industrial security clearance case involves the adjudication of the security eligibility of officers and employees of defense contractors under Executive Order 10865 and DoD Directive 5220.6.
Know where you stand. Our experienced staff of professionals is here to assist you and put your mind at ease. Most, if not all, of these topics or issues can be mitigated and be made to appear less severe. Know the questions that will be asked by the investigators. Know which questions will not be asked. Most of all, know the appropriate responses to the topic or issue questions. Knowing all of this information will allow you to better position yourself and to significantly increase your chances of successfully being granted your security clearance. Be prepared. Your current or future job is at stake.
Additional Resources
DoD Directive 5200.2- R, Personnel Security Program
DoD Directive 5220.6, Defense Industrial Personnel Security Clearance Review Program
DoD Directive 5220.22, National Industrial Security Program
Executive Order 10865, Safeguarding Classified Information within Industry
Executive Order 12968, Access to Classified Information
Adjudicative Desk Reference (ADR)
Army Regulation 380-67 (Army PSP)
SECNAV M-5510.30 (Navy PSP)
AFI31-501 (Air Force PSP)
Selected Executive Orders on National Security
Electronic Code of Federal Regulations